Protect Boot & Single user mode
as a physical security is the main factor in our security perspective
we all need to protect unauthorised access to our Linux box after we protect bios
and we all know that anyone can rest the root password via accessing the single mode
so we have 3 ways 1st thing to disable single user mode entirely 2nd adding a password 3rd encrypt the disk with luks
single use mode configuration located under /etc/sysconfig/init
|
1 2 3 4 5 6 7 8 9 10 11 |
BOOTUP=color RES_COL=60 MOVE_TO_COL="echo -en \\033[${RES_COL}G" SETCOLOR_SUCCESS="echo -en \\033[0;32m" SETCOLOR_FAILURE="echo -en \\033[0;31m" SETCOLOR_WARNING="echo -en \\033[0;33m" SETCOLOR_NORMAL="echo -en \\033[0;39m" PROMPT=yes AUTOSWAP=no ACTIVE_CONSOLES=/dev/tty[1-6] SINGLE=/sbin/sushell |
the last line of the init configuration instructs the user shell for single user mode
sushell this shell allows access with full root privilege we can change the shell type to control the single user mode
if we sit it /sbin/nologin no single user mode will be activated on the boot and the machine will continue booting to default run level 😉
we can set it to sulogin to make boot asks for the root password before it continues to give a full root access
|
1 2 |
Give root password for maintenance (or type Control-D to continue): |
we can add more password layer for grub configuration via adding password –encrypt HASH from grub-crypt command
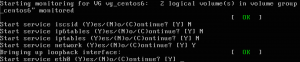
one important thing an attacker can manipulate boot start services by pressing (i) in the boot sequence
an attacker can disable any running service example I disabled iptables in the boot 😀
we can protect from this disaster by disable hotkeys in /etc/sysconfig/init
|
1 |
PROMPT=no |
protect the console from reboot via ctrl-alt-delete
an attacker can press ctrl-alt-delete to your machine to make it reboot
to disable it we need to change the behaviour of this intercept in /etc/init/control-alt-delete.conf
|
1 2 3 4 5 6 7 8 9 10 11 |
# control-alt-delete - emergency keypress handling # # This task is run whenever the Control-Alt-Delete key combination is # pressed. Usually used to shut down the machine. # # Do not edit this file directly. If you want to change the behaviour, # please create a file control-alt-delete.override and put your changes there. start on control-alt-delete #exec /sbin/shutdown -r now "Control-Alt-Delete pressed" |
by adding a comment to the exec line to disable reboot
Thank you for sharing wonderful information with us to get some idea about that content